Disini akan mengkombinasikan Layer 2 tunneling protocol L2TP yang akan diproteksi dengan IPSec dengan software strongswan.
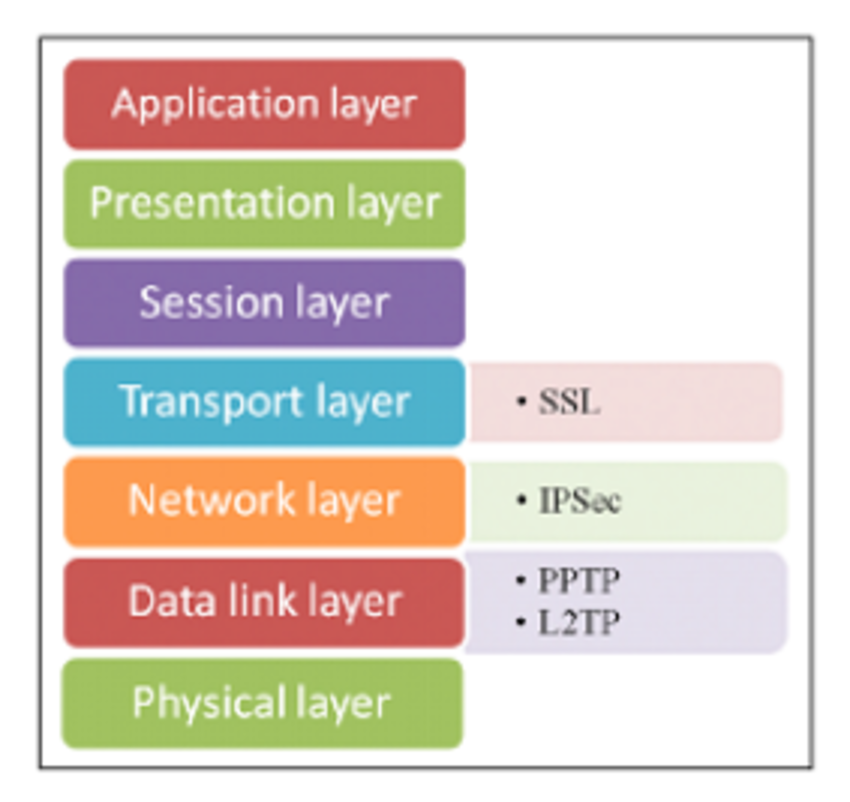
Selain itu strongswan juga bisa berdiri sendiri tanpa xl2tpd jika anda menginginkan VPN tipe lain IPSec yang di layer 3, FYI seperti gambar dibawah lokasi berdasarkan OSI layer, kalau misalnya OpenVPN berarti menggunakan SSL.
 |
| https://www.researchgate.net/publication/287458379_Efficiency_Consideration_for_Data_Packets_Encryption_within_Wireless_VPN_Tunneling_for_Video_Streaming |
xl2tpd is an open source implementation of the L2TP tunneling protocol (RFC2661). xl2tpd is forked from l2tpd and is maintained by Xelerance Corporation.
Teori
The main purpose of this protocol is to tunnel PPP frames through IP networks. It implements both LAC and LNS role in the L2TP networking architecture.
StrongSwan is a comprehensive implementation of the Internet Key Exchange (IKE) protocols that allows securing IP traffic in policy- and route-based IPsec scenarios from simple to very complex.
xl2tpd is a fork of l2tpd Layer 2 Tunneling Protocol (L2TP) daemon that can be used to transfer frames of OSI layer 2 protocols through an IP tunnel. While it provides authentication via CHAP or PAP it does not provide encryption itself and should therefore be externally secured (via IPSEC).
https://packages.gentoo.org/packages/net-dialup/xl2tpd
How it works https://www.techtarget.com/searchnetworking/definition/Layer-Two-Tunneling-Protocol-L2TP
Konfigurasi
apt install strongswan xl2tpd
/etc/ipsec.conf
conn L2TP-VPN
left=210.100.2.1 ; Public IP Address in Server Side
leftprotoport=17/1701
right=%any
rightprotoport=17/%any
authby=secret
type=transport
auto=add
/etc/ipsec.secrets
: PSK Pa$$worD
/etc/xl2tpd/xl2tpd.conf
[global]
access control = no
[lns default]
ip range = 192.168.1.100-192.168.1.199 ; for Client
local ip = 192.168.1.1
require authentication = yes
name = l2tpd
ppp debug = yes
pppoptfile = /etc/ppp/ppp-options.xl2tpd
cp /usr/share/doc/xl2tpd/examples/ppp-options.xl2tpd /etc/ppp
/etc/ppp/ppp-options.xl2tpd
ms-dns 192.168.1.250 ; Internal DNS Server for VPN Client
require-mschap-v2
#crtscts
#lock
/etc/ppp/chap-secrets
# Secrets for authentication using CHAP
# client server secret IP addresses
user01 * password *
user02 * password *
Setelah melakukan konfigurasi diatas selanjutnya bisa konek di sisi linux client dengan network manager GUI, atau dari windows bisa memakai bawaan network manager tanpa menginstall software client tambahan seperti openvpn.
Thanks.
Comments
Post a Comment